Understanding Electronic Health Records, the HIPAA Security Rule, and Cyber security.

To support patient care, providers store electronic Protected Health Information (ePHI) in a variety of electronic systems, not just Electronic Health Records (EHRs). Knowing this, providers must remember that all electronic systems are vulnerable to cyber-attacks and must consider in their security efforts all of their systems and technologies that maintain ePHI.46 (See Chapter 6 for more information about security risk analysis.)
While a discussion of ePHI security goes far beyond EHRs, this chapter focuses on EHR security in particular.
These Security Rule safeguards can help health care providers avoid some of the common security gaps that could lead to cyber-attack intrusions and data loss. Safeguards can protect the people, information, technology, and facilities that health care providers depend on to carry out their primary mission: caring for their patients.
The Security Rule has several types of safeguards and requirements which you must apply:
Administrative Safeguards
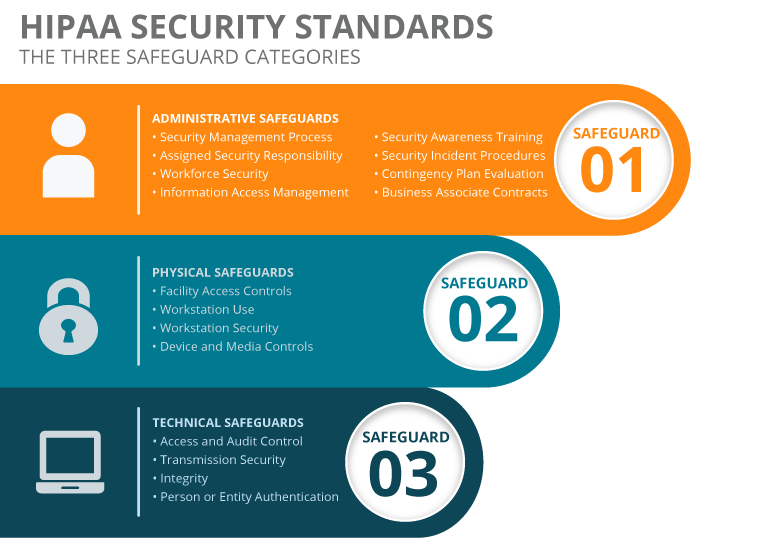
Administrative safeguards are administrative actions, policies, and procedures to prevent, detect, contain, and correct security violations. Administrative safeguards involve the selection, development, implementation, and maintenance of security measures to protect ePHI and to manage the conduct of workforce members in relation to the protection of that information. A central requirement is that you perform a security risk analysis that identifies and analyzes risks to ePHI and then implement security measures to reduce the identified risks.
Physical Safeguards
These safeguards are physical measures, policies, and procedures to protect electronic information systems and related buildings and equipment from natural and environmental hazards and unauthorized intrusion.54 These safeguards are the technology and the policies and procedures for its use that protect ePHI and control access to it.
HIPAA Technical Safeguards
What are technical safeguards?
According to the HIPAA Security Rule, technical safeguards are “the technology and the policy and procedures for its use that protect electronic protected health information and control access to it.” Essentially, a covered entity must use any security measures that allow it to reasonably and appropriately implement the necessary standards for protection. Moreover, a covered entity must determine which security measures and specific technologies are reasonable and appropriate.
For example, a smaller healthcare organization might not need the same type of computer malware program as it is likely operating on a less complicated system than a large health information exchange.
For example, a smaller healthcare organization might not need the same type of computer malware program as it is likely operating on a less complicated system than a large health information exchange.
Access and audit control requirements
Two of the major aspects of strong technical safeguards are within the access and audit control requirements. For example, a facility needs to determine the access control capability of all information systems with ePHI and ensure that system activity can be traced to a specific user. It is also critical to create a formal policy for access control that will guide the development of procedures. Implementing a mechanism to encrypt and decrypt ePHI will also be beneficial. This can help healthcare organizations determine if the chosen encryption is appropriate for storing and maintaining ePHI while it’s being stored and while it’s being transmitted.
In terms of audit control requirements, facilities must implement hardware, software, and/or procedural mechanisms that record and examine activity in information systems that contain or use ePHI.
A covered entity also needs to document and communicate audit control procedures and protocols. Employees at all levels must understand how often audits will take place, how the results will be analyzed, what the organization’s sanction policies are for employee violations, and where audit information will reside.
Authentication and integrity
Covered entities must also institute policies and procedures to protect ePHI from improper alteration or destruction. These integrity controls can be created by figuring out how outside sources might jeopardize information integrity. Furthermore healthcare organizations should determine how to secure that data while it’s being stored – at rest. For example, error-correcting memory, magnetic disk storage, digital signatures, and check sum technology are all electronic mechanisms that can be used for authentication.
Overall, a comprehensive view needs to be taken when confirming user identities. Healthcare organizations must ensure that a user who is viewing ePHI is actually authorized to do so. Even guaranteeing the validity of a transmission source or access privileges to patient data can go a long way in building strong technical safeguards.
Securing the data ‘in motion’
Secure data transmission is essential for healthcare organizations, especially with the growth of electronic medical records (EMR) and health information exchanges (HIEs). How can covered entities function properly within an HIE if it cannot securely transmit a patient’s medical records to another facility?
According to the National Institute of Standards and Technology (NIST) HIPAA Security Rule Guide, organizations must encrypt ePHI in motion, while also making sure the encryption is reasonable and appropriate. Moreover, covered entities need to ensure the chosen encryption is cost-effective, feasible, and efficient. Staff members have to be trained in all aspects of the chosen encryption option so they can properly use their acquired skill set.
Comprehensive HIPAA safeguards
When technical safeguards are properly applied with physical and administrative safeguards, a healthcare organization will be much better prepared for numerous types of data breaches. Data encryption and firewalls are just the beginning, as employees must be trained properly and understand how best to handle ePHI.
Technical safeguards must evolve along with healthcare technology. But, if an organization takes the necessary steps to keep pace, it will have a much better chance at keeping ePHI from falling into the wrong hands.
Organizational Standards
These standards require a CE to have contracts or other arrangements with BAs that will have access to the CE’s ePHI. The standards provide the specific criteria required for written contracts or other arrangements.
Policies and Procedures
These standards require a CE to adopt reasonable and appropriate policies and procedures to comply with the provisions of the Security Rule. A CE must maintain, until six years after the date of their creation or last effective date (whichever is later), written security policies and procedures and written records of required actions, activities, or assessments. A CE must periodically review and update its documentation in response to environmental or organizational changes that affect the security of ePHI.
Resources
HIPAA Requirements,48 in detail
HIPAA Privacy Rule,49 in detail
HIPAA Security Rule,50 in detail
How to Keep Your Patients’ Health Information Secure with an HER

Your practice is responsible for taking the steps needed to protect the confidentiality, integrity, and availability of ePHI maintained in your EHR.
Having an EHR affects the types and combinations of safeguards you will need to keep your patients’ health information confidential. EHRs also bring new responsibilities for safeguarding your patients’ health information in an electronic form.
To uphold patient trust as your practice continues to adopt and use an EHR or other electronic technology for collection and use of ePHI, and to comply with HIPAA Security Rule and Meaningful Use requirements, your practice must conduct a security risk analysis (sometimes called “security risk assessment”). (See Chapter 6 for more discussion on security risk analysis.) The risk analysis process will guide you through a systematic examination of many aspects of your health care practice to identify potential security weaknesses and flaws.
Many health care providers will need to make changes to reduce risks and to comply with the HIPAA Rules and Meaningful Use requirements. Fortunately, properly configured and certified EHRs58 can provide more protection to ePHI than paper files provided. (See Step 5A in Chapter 6 for more information about using electronic capabilities to.
Your EHR Software and Hardware
Most EHRs and related equipment have security features built in or provided as part of a service, but they are not always configured or enabled properly.
As the guardian of ePHI, it is up to you — along with your designated staff members — to learn about these basic features and ensure they are functioning and are updated when necessary. You and your staff must keep up-to-date with software upgrades and available patches.
Remember, security risk analysis and mitigation is an ongoing responsibility for your practice. Vigilance should be part of your practice’s ongoing activities.
According to the HIPAA Security Rule <
There are several overarching standards discussed within the HIPAA technical safeguards:
Access Control
Giving users rights and/or privileges to access and perform functions using information systems, applications, programs, or files.
Audit Controls
Hardware, software, and/or procedural mechanisms that record and examine information system activity that contain or use ePHI.
Integrity Controls
Implementing policies and procedures for ePHI protection against alteration or destruction, person or Entity Authentication ensuring a person’s identity before giving him or her ePHI access.
Transmission Security
Guarding against unauthorized ePHI access when data is transmitted over an electronic communications network.
Overall, technical safeguards are technology and its related policies and procedures that are implemented to help ensure ePHI security.

