HIPAA IT Compliance
HIPAA IT compliance is primarily concerned with ensuring all the provisions of the HIPAA Security Rule are followed and all elements on your HIPAA compliance checklist are covered. Risk assessment and management is a key consideration for HIPAA IT compliance.One way to help ensure risks are identified and appropriate controls are implemented as part of your HIPAA IT compliance program is to adopt the NIST Cyber security Framework.The NIST Cyber security Framework will help you to prevent data breaches, and detect and respond to attacks in a HIPAA compliant manner when attacks do occur. HIPAA IT compliance concerns all systems that are used to transmit, receive, store, or alter electronic protected health information, any system or software that ‘touches’ ePHI electronic protected health information must incorporate appropriate security protections to ensure the confidentiality, integrity, and availability of ePHI.One element of the HIPAA compliance checklist that is often low down on the priority list is monitoring ePHI access logs regularly. Inappropriate accessing of ePHI by healthcare employees is common, yet many covered entities fail to conduct regular audits and inappropriate access can continue for months or sometimes years before it is discovered.
 HIPAA Compliance Checklist for IT
HIPAA Compliance Checklist for IT
In addition to the rules and regulations that appear on our HIPAA compliance checklist originating from acts of legislation, there are several mechanisms that IT departments can implement to increase the security of Protected Health Information.Potential lapses in security due to the use of personal mobile devices in the workplace can be eliminated by the use of a secure messaging solution. Secure messaging solutions allow authorized personnel to communicate PHI – and send attachments containing PHI – via encrypted text messages that comply with the physical, technical and administrative safeguards of the HIPAA Security Rule.Email is another area in which potential lapses in security exist. Emails containing PHI that are sent beyond an internal fire walled served should be encrypted. It should also be considered that emails containing PHI are part of a patient´s medical record and should therefore be archived securely in an encrypted format for a minimum of six years.As medical records can attract a higher selling price on the black market than credit card details, defenses should be put in place to prevent phishing attacks and the inadvertent downloading of malware. Several recent HIPAA breaches have been attributed to criminals obtaining passwords to EMRs or other databases, and healthcare organizations can mitigate the risk of this happening to them with a web content filter.
Additional HIPAA IT Requirements

As well as the technological regulations mentioned above, there are many miscellaneous HIPAA IT requirements that are easy to overlook – for example the facility access rules within the physical safeguards of the Security Rule. These HIPAA IT requirements may inadvertently be discounted if the IT Department has no responsibility for the physical security of its servers, and it will be the HIPAA Security Officer´s role to establish responsibility.Other areas of the HIPAA IT requirements frequently overlooked include Business Associate Agreements with SaaS providers and hosting companies who may have access to PHI via the services they provide.The same applies to software developers who build eHealth apps that will transmit PHI. There has to be a Business Associate Agreement in place with any health care provider distributing the app in order to be compliant with the HIPAA IT requirements.
The Importance of Data Encryption
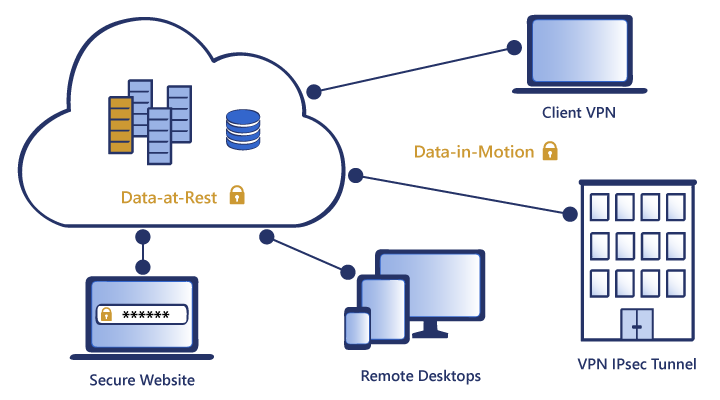
The vast majority of ePHI breaches result from the loss or theft of mobile devices containing unencrypted data and the transmission of unsecured ePHI across open networks.
Breaches of this nature are easily avoidable if all ePHI is encrypted. Although the current HIPAA regulations do not demand encryption in every circumstance, it is a security measure which should be thoroughly evaluated and addressed. Suitable alternatives should be used if data encryption is not implemented. Data encryption renders stored and transmitted data unreadable and unusable in the event of theft.
HIPAA Audit Checklist
The final area of our HIPAA compliance checklist concerns a HIPAA audit checklist.The passage of the HIPAA Enforcement Rule created a viable way in which HHR could monitor HIPAA compliance.It was found that a Covered Entity or Business Associate had made no attempt to comply with HIPAA, HHR could issue fines even if no breach of PHI had occurred.
In order to help Covered Entities and Business Associates compile a HIPAA audit checklist, HHR has released audit protocols for the first two rounds of audits.You can find out more about the audit protocols on our dedicated HIPAA Audit Check list page, and – if you scroll down to the bottom of the page – the latest updates on the audits and details about documentation requests.
Please review our info graphic to see the cost of failing to complete and implement a HIPAA compliance checklist.
LEARN MORE <

